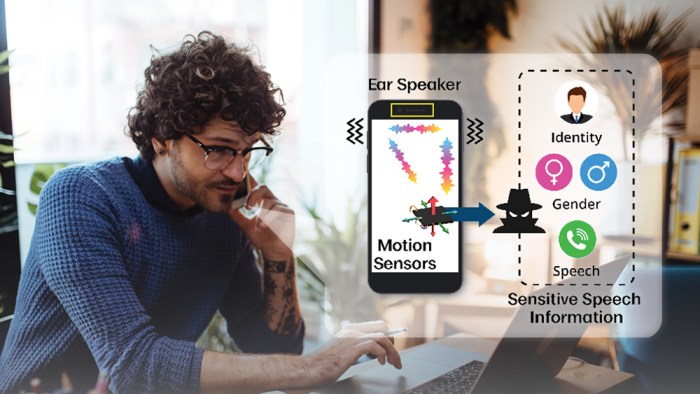
Smartphone speech security is a critical concern in today’s digital world, where our voices are increasingly used for communication, authentication, and data access. From eavesdropping to voice spoofing, threats targeting speech interactions on smartphones are becoming more sophisticated and pervasive. This article delves into the multifaceted landscape of smartphone speech security, exploring the vulnerabilities, security measures, and best practices to safeguard your voice.
The reliance on smartphones for communication and data storage has surged, making them integral to our daily lives. However, this dependence comes with inherent vulnerabilities, particularly when it comes to speech interactions. Speech data, unlike text or images, is uniquely sensitive, as it can reveal personal information, emotions, and even physical characteristics. Therefore, ensuring the security of speech interactions on smartphones is paramount.
Smartphone Speech Security
Smartphones have become indispensable tools for communication and data storage, deeply integrated into our daily lives. From making calls and sending messages to accessing sensitive information and managing finances, smartphones have become extensions of ourselves. However, this increasing reliance on smartphones has brought to light inherent vulnerabilities associated with speech interactions.
The Importance of Speech Security
Speech security is crucial for safeguarding sensitive information exchanged through smartphones. Speech recognition technology, while incredibly convenient, can be susceptible to various security risks, including:
- Eavesdropping: Malicious individuals can intercept and listen to private conversations without authorization, potentially compromising sensitive data.
- Voice Cloning: Advanced techniques can create synthetic voices that closely resemble real individuals, enabling impersonation and unauthorized access to secure systems.
- Speech Recognition Attacks: Attackers can exploit vulnerabilities in speech recognition systems to manipulate or alter speech commands, leading to unintended actions or unauthorized access.
Security Measures Implemented in Smartphones
Smartphones have become an integral part of our lives, storing sensitive information and facilitating communication. This has led to increased concerns about the security of these devices, especially when it comes to protecting speech interactions. Smartphone manufacturers have implemented various security measures to safeguard user privacy and prevent unauthorized access to voice data.
Encryption Protocols for Voice Calls and Messages
Encryption is a fundamental security measure that protects the confidentiality of voice calls and messages. Encryption algorithms transform data into an unreadable format, making it incomprehensible to anyone without the decryption key.
- End-to-End Encryption: This is the most secure type of encryption, where only the sender and receiver have the keys to decrypt the data. End-to-end encryption ensures that even the service provider cannot access the content of the communication. Popular messaging apps like WhatsApp and Signal use end-to-end encryption for their voice and text messages.
- Transport Layer Security (TLS): This protocol secures communication between a smartphone and a server, ensuring that data is transmitted securely over the internet. TLS is commonly used for voice calls and messages over the internet, including VoIP calls and video conferencing.
Voice Authentication and Biometric Verification
Voice authentication and biometric verification provide an additional layer of security by verifying the identity of the user before granting access to sensitive data or functions.
- Voice Recognition: This technology analyzes the unique characteristics of a person’s voice to authenticate their identity. Voice recognition can be used to unlock a smartphone, authorize payments, or access specific apps.
- Facial Recognition: This technology uses facial features to identify individuals. Facial recognition can be used to unlock a smartphone, verify identity for online transactions, or access secure areas.
- Fingerprint Scanning: This technology uses a fingerprint sensor to verify the identity of a user. Fingerprint scanning is commonly used to unlock smartphones, authorize payments, or access secure apps.
Secure Storage and Access Control for Voice Recordings, Smartphone speech security
Smartphones often store voice recordings, such as voice memos, voicemail messages, and voice assistant interactions. To protect this data, smartphones implement secure storage mechanisms and access controls.
- Secure Storage: Voice recordings are typically stored in encrypted storage containers that are only accessible by authorized users.
- Access Control: Access to voice recordings is typically restricted to the device owner, with options to set passwords or biometrics for authentication.
Privacy Settings for Voice Assistant Usage and Data Sharing
Voice assistants, such as Siri, Google Assistant, and Alexa, are becoming increasingly popular. However, they collect and analyze user data, raising privacy concerns. Smartphone manufacturers provide privacy settings to control the usage and data sharing of voice assistants.
- Data Collection Control: Users can choose to limit the data that voice assistants collect, such as location data, contact information, and browsing history.
- Voice Recording Access: Users can control whether voice assistants record and store their voice interactions.
- Data Sharing Preferences: Users can control how their voice data is shared with third-party apps and services.
Legal and Ethical Considerations
The implementation of robust speech security measures on smartphones raises crucial legal and ethical considerations. These considerations encompass data privacy regulations, the balance between security and user convenience, and the potential misuse of speech recognition technology.
Data Privacy Regulations and User Consent
Data privacy regulations, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States, impose stringent requirements on how personal data, including voice recordings, can be collected, stored, and processed. Smartphone manufacturers and speech recognition service providers must obtain explicit user consent before collecting and using voice data.
- This consent must be informed, meaning users must be fully aware of what data is being collected, how it will be used, and for how long it will be retained.
- Users must also have the right to access, rectify, or delete their data, as well as the right to restrict or object to its processing.
Case Studies and Examples
This section explores real-world examples and case studies that demonstrate the impact of speech security threats on smartphone users. Understanding these incidents can highlight the vulnerabilities and consequences of inadequate speech security measures.
High-Profile Data Breaches Involving Voice Recordings
Data breaches involving voice recordings can have severe consequences for individuals and organizations.
- In 2019, a major data breach at a popular ride-hailing company exposed millions of user voice recordings, including sensitive conversations between drivers and passengers. This incident raised concerns about the security of voice data collected by smartphone apps and the potential for misuse.
- Another notable case involved a social media platform that was accused of storing and accessing user voice recordings without their explicit consent. This incident sparked public outcry and raised questions about the ethical implications of collecting and using voice data.
Instances of Voice Spoofing or Impersonation Attacks Leading to Financial Loss
Voice spoofing attacks exploit vulnerabilities in voice recognition systems to impersonate legitimate users. These attacks can lead to financial losses and identity theft.
- A recent study by researchers at the University of California, Berkeley, demonstrated the feasibility of using deep learning techniques to create highly realistic voice spoofs. The study showed that attackers could use these spoofs to bypass voice authentication systems and gain unauthorized access to sensitive accounts.
- In 2020, a British businessman was reportedly defrauded of millions of dollars in a voice spoofing attack. The attacker used sophisticated technology to mimic the voice of the businessman’s CEO, convincing the businessman to transfer funds to a fraudulent account.
Legal Disputes Regarding the Use of Voice Data for Advertising or Profiling
The use of voice data for advertising and profiling raises complex legal and ethical considerations.
- Several lawsuits have been filed against smartphone manufacturers and app developers for allegedly collecting and using user voice data without their consent. These lawsuits argue that the collection and use of voice data violate privacy laws and raise concerns about the potential for discrimination and targeted advertising.
- In 2021, the European Union’s General Data Protection Regulation (GDPR) was updated to include specific provisions related to the processing of voice data. These provisions aim to strengthen user rights and protect voice data from unauthorized access and use.
Conclusion
The integration of speech technology into smartphones has revolutionized communication and convenience. However, this advancement comes with inherent security vulnerabilities that require ongoing attention and proactive measures. This discussion has highlighted the critical importance of safeguarding speech data on smartphones, ensuring user privacy, and mitigating potential risks.
The Importance of Ongoing Security Measures
The evolving nature of cyber threats necessitates a continuous evolution of security measures. Developers and researchers must collaborate to stay ahead of emerging vulnerabilities and implement robust security protocols. This includes:
- Regular software updates to patch vulnerabilities and enhance security features.
- Implementing secure authentication mechanisms, such as biometrics or multi-factor authentication, to prevent unauthorized access.
- Adopting encryption techniques to protect speech data both in transit and at rest.
- Developing advanced detection and prevention systems to identify and mitigate malicious activities targeting speech data.
Closing Summary: Smartphone Speech Security
In conclusion, smartphone speech security is a multifaceted issue that demands a comprehensive approach. By understanding the vulnerabilities, implementing appropriate security measures, and staying informed about emerging threats, users can significantly enhance their protection. Collaboration between researchers, developers, and policymakers is crucial to ensure the secure and responsible use of speech technology on smartphones, fostering a future where voice interactions are both convenient and secure.
Smartphone speech security is crucial, especially as our devices store sensitive information. It’s important to consider the security features offered by different models, including those related to voice recognition and data encryption. For a detailed look at the features of various smartphones, including camera capabilities, check out Compare Smartphone Cameras: A Comprehensive Guide.
This guide can help you make an informed decision about the smartphone that best meets your security and privacy needs.
 Informatif Berita Informatif Terbaru
Informatif Berita Informatif Terbaru